What You'll Learn
This quick-start guide walks you through running OpenClaw in Docker with scoped secrets from API Stronghold. By the end, you’ll have an isolated AI agent that only has access to the specific API keys it needs — no more, no less.
This is a companion tutorial to our comprehensive guide on Securing OpenClaw with Scoped Secrets. That post covers the full architecture, multiple setup options, and advanced configurations. This one gets you running in 10 minutes.
What Is Docker? (30-Second Primer)
If you’re new to Docker, here’s the quick version: Docker lets you run applications in containers — isolated environments that bundle everything an app needs to run. Think of it like a lightweight virtual machine.
For AI agents like OpenClaw, Docker provides:
- Isolation — the agent can’t access your host system’s files or other credentials
- Reproducibility — the same container runs identically everywhere
- Security boundaries — if something goes wrong, the blast radius is limited
Prerequisites
Before starting, you need:
- Docker Desktop installed (download here)
- An API Stronghold account (sign up free)
- Your API keys already added to API Stronghold with a deployment profile and user group configured (see Steps 1-5 in the main guide)
- An Anthropic API key for OpenClaw’s AI model
Do NOT use your Claude Max subscription
Important: Do not use your Claude Pro or Max consumer subscription with OpenClaw or any automated AI agent. Anthropic’s terms of service prohibit using consumer subscriptions for automated or programmatic access, and users have reported account bans for doing so. You need a separate Anthropic API key from console.anthropic.com with pay-as-you-go billing. This is a different product from the claude.ai consumer subscription.
Already have API Stronghold set up?
If you’ve already added your keys, created a deployment profile, set up key exclusions, and have an API user token, skip ahead to Build the Gateway.
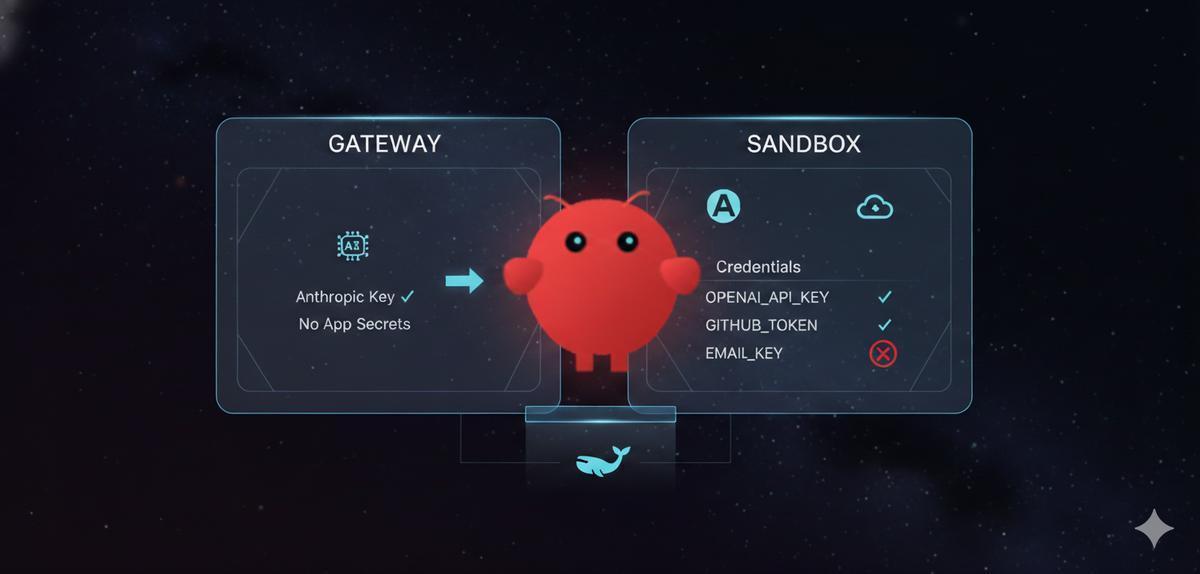
The Architecture (What We’re Building)
OpenClaw uses a dual-container model:
┌─────────────────────────────────────────────────────────┐
│ Your Machine │
│ │
│ ┌─────────────────────┐ ┌─────────────────────┐ │
│ │ Gateway Container │────▶│ Sandbox Container │ │
│ │ (AI model creds) │ │ (your API keys) │ │
│ │ │ │ │ │
│ │ Anthropic key only │ │ OPENAI_API_KEY ✓ │ │
│ │ No app secrets │ │ GITHUB_TOKEN ✓ │ │
│ └─────────────────────┘ │ EMAIL_KEY ✗ │ │
│ │ └─────────────────────┘ │
│ │ Docker socket │
│ ▼ │
│ ┌─────────────────────┐ │
│ │ Docker Daemon │ │
│ └─────────────────────┘ │
└─────────────────────────────────────────────────────────┘The gateway talks to the AI model (Claude/GPT) and manages sessions. The sandbox runs the agent’s tools and has your application secrets. They’re separate containers — a compromise of one doesn’t expose both sets of credentials.
Step 1: Build the Gateway
Clone OpenClaw and build the gateway image with the Docker CLI included:
git clone https://github.com/openclaw/openclaw.git
cd openclaw
# Build gateway with Docker CLI (needed to spawn sandbox containers)
OPENCLAW_DOCKER_APT_PACKAGES="docker.io" docker build \
--build-arg "OPENCLAW_DOCKER_APT_PACKAGES=docker.io" \
-t openclaw:local .What's happening here?
The --build-arg tells Docker to install the docker.io package inside the gateway image. The gateway needs the Docker CLI to create and manage sandbox containers.
Step 2: Build the Sandbox
Build the base sandbox image, then create a custom one with the API Stronghold CLI:
# Build the base sandbox image
scripts/sandbox-setup.shNow create a custom sandbox image. First, authenticate the CLI on your host machine:
macOS / Linux:
curl -fsSL https://www.apistronghold.com/cli/install.sh | shWindows (Command Prompt):
curl -fsSL https://www.apistronghold.com/cli/install.cmd -o install.cmd && install.cmd && del install.cmdThe Windows installer places the CLI in %USERPROFILE%\.api-stronghold\bin\ and adds it to your PATH automatically. Restart your terminal after installing. For more details, see the CLI installation guide.
Then authenticate with your API user token:
api-stronghold-cli auth api-user --token YOUR_API_USER_TOKENCreate a Dockerfile.sandbox in the openclaw directory:
FROM openclaw-sandbox:bookworm-slim
# Install the API Stronghold CLI
RUN curl -fsSL https://www.apistronghold.com/cli/install.sh | sh
# Copy your pre-authenticated credentials
COPY .api-stronghold/ /var/lib/nova/.api-stronghold/
RUN chown -R nova:nova /var/lib/nova/.api-stronghold
USER novaCopy your credentials and build:
# Copy credentials into build context
cp -r ~/.api-stronghold .api-stronghold
# Build the custom sandbox
docker build -f Dockerfile.sandbox -t openclaw-sandbox-secure:latest .
# Clean up (don't commit credentials!)
rm -rf .api-strongholdStep 3: Configure the Gateway
Create a docker-compose.override.yml file (this won’t conflict with OpenClaw’s tracked compose file):
# docker-compose.override.yml
services:
openclaw-gateway:
user: root
environment:
# Must match your actual home directory for volume mounts to work
HOME: /Users/youruser # Change this!
volumes:
- ${OPENCLAW_CONFIG_DIR}:/Users/youruser/.openclaw
- ${OPENCLAW_WORKSPACE_DIR}:/Users/youruser/.openclaw/workspace
- ${OPENCLAW_CONFIG_DIR}/sandboxes:/Users/youruser/.openclaw/sandboxes
- /var/run/docker.sock:/var/run/docker.sockFinding Your Home Directory
You must replace /Users/youruser with your actual home directory path. To find it:
# macOS / Linux
echo $HOME
# Example output: /Users/kenny or /home/kenny
# Windows (PowerShell)
echo $env:USERPROFILE
# Example output: C:\Users\kennyUse this exact path in three places:
- The
HOMEenvironment variable - All three volume mount destinations (the part after the colon)
For example, if your home directory is /Users/kenny:
environment:
HOME: /Users/kenny
volumes:
- ${OPENCLAW_CONFIG_DIR}:/Users/kenny/.openclaw
- ${OPENCLAW_WORKSPACE_DIR}:/Users/kenny/.openclaw/workspace
- ${OPENCLAW_CONFIG_DIR}/sandboxes:/Users/kenny/.openclaw/sandboxes
- /var/run/docker.sock:/var/run/docker.sockWhy does HOME matter? (This is the #1 setup gotcha)
This is the trickiest part of the Docker setup and catches most people. Here’s what happens:
- The gateway container runs as
root, so its defaultHOMEis/root - When the gateway spawns a sandbox, it tells Docker to mount
$HOME/.openclaw/sandboxes/... - Docker Desktop resolves that path on the host machine, not inside the container
- If
HOME=/rootinside the gateway, Docker looks for/root/.openclaw/sandboxes/on your Mac — which doesn’t exist - Docker fails with:
Mounts denied: path is not shared from the host
By setting HOME to your actual macOS/Linux home directory, the paths match and mounts work correctly.
Step 4: Configure the Sandbox
Edit ~/.openclaw/openclaw.json (create it if it doesn’t exist):
{
"agents": {
"defaults": {
"sandbox": {
"mode": "all",
"docker": {
"image": "openclaw-sandbox-secure:latest",
"network": "bridge",
"setupCommand": "mkdir -p /workspace/.api-stronghold && cp /var/lib/nova/.api-stronghold/config.yaml /workspace/.api-stronghold/config.yaml"
}
}
}
},
"gateway": {
"controlUi": {
"allowInsecureAuth": true
}
}
}What these settings do:
| Setting | Purpose |
|---|---|
mode: "all" | Sandbox every session, including the main agent |
network: "bridge" | Allow outbound network access (CLI needs to reach API Stronghold) |
setupCommand | Copy credentials to the sandbox’s working directory on startup |
allowInsecureAuth | Let you access the Control UI over HTTP (local dev only) |
Step 5: Start the Gateway
Run the interactive setup:
./docker-setup.shWhen prompted:
- Acknowledge the risk warning
- Choose QuickStart for onboarding mode
- Select Anthropic setup-token for auth (run
claude setup-tokenin another terminal) - Skip channels configuration
- Say No to installing the gateway daemon (Docker manages it)
After setup completes, note the gateway token displayed in the output.
Step 6: Verify It Works
Open the Control UI at http://127.0.0.1:18789/?token=YOUR_GATEWAY_TOKEN.
Start a new session and ask the agent:
Can you run
api-stronghold-cli key listto show what API keys are available?
You should see only the keys your API Stronghold user group is authorized to access. Excluded keys (email, billing, etc.) won’t appear.
Check both containers are running:
docker ps | grep openclawYou should see both the gateway and sandbox containers.
What You’ve Built
Your AI agent now:
- Runs in an isolated Docker container
- Has access only to the specific API keys you’ve allowed
- Cannot see or use keys that are excluded at the group level
- Gets fresh credentials on each session start
- Has no credentials stored on disk inside the container
Next Steps
This quickstart uses the simplest approach: loading secrets at container startup. For more advanced setups, including:
- Giving the agent a skill to refresh credentials mid-session
- Full CLI access for DevOps agents
- Network lockdown for production
- Troubleshooting common issues
See the complete guide: Securing OpenClaw with Scoped Secrets.
Getting Started with API Stronghold
Don’t have an API Stronghold account yet?
- Sign up free
- Add your API keys on the Keys page
- Create a deployment profile and configure key exclusions
- Create an API user (1 free per org)
- Follow this tutorial to run your agent securely
Your AI agent gets exactly the keys it needs — and nothing it doesn’t.